New Feature Alert - CISO DashboardCheckout Now
350+
Integrated Applications
3M+
Identities protected
5$
per user saved for Governance and Reports
KEY ADVANTAGES
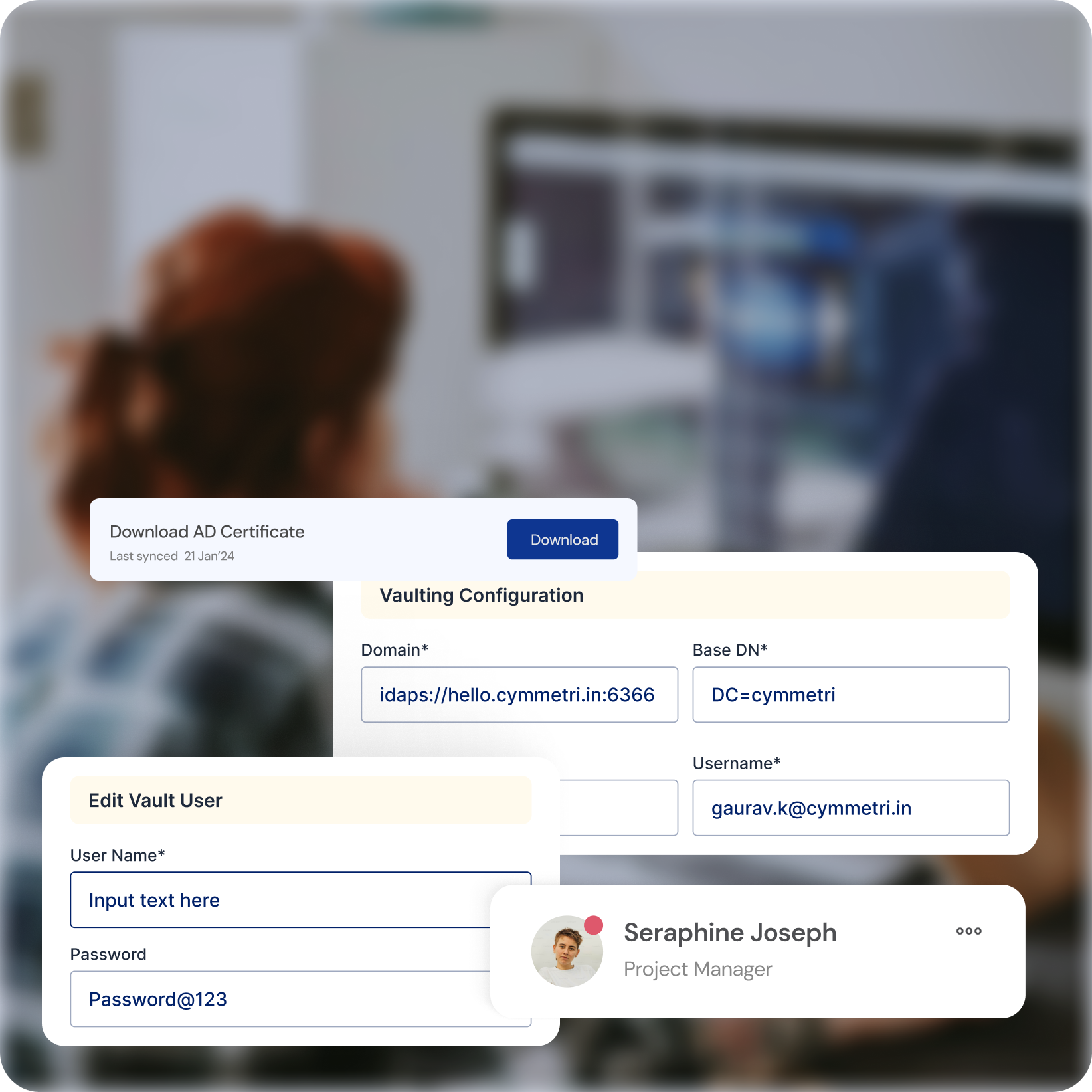
Centralized Password Management
Secure Vault
Eliminate the risk of weak passwords and stolen credentials by storing and managing privileged account passwords in a centralized, encrypted vault
Automated Rotation
Enforce strong password policies with automatic rotation and enforce regular password changes to prevent unauthorized access.
Reduced Complexity
Simplify password management for IT teams and eliminate the need for manual password resets.
KEY ADVANTAGES
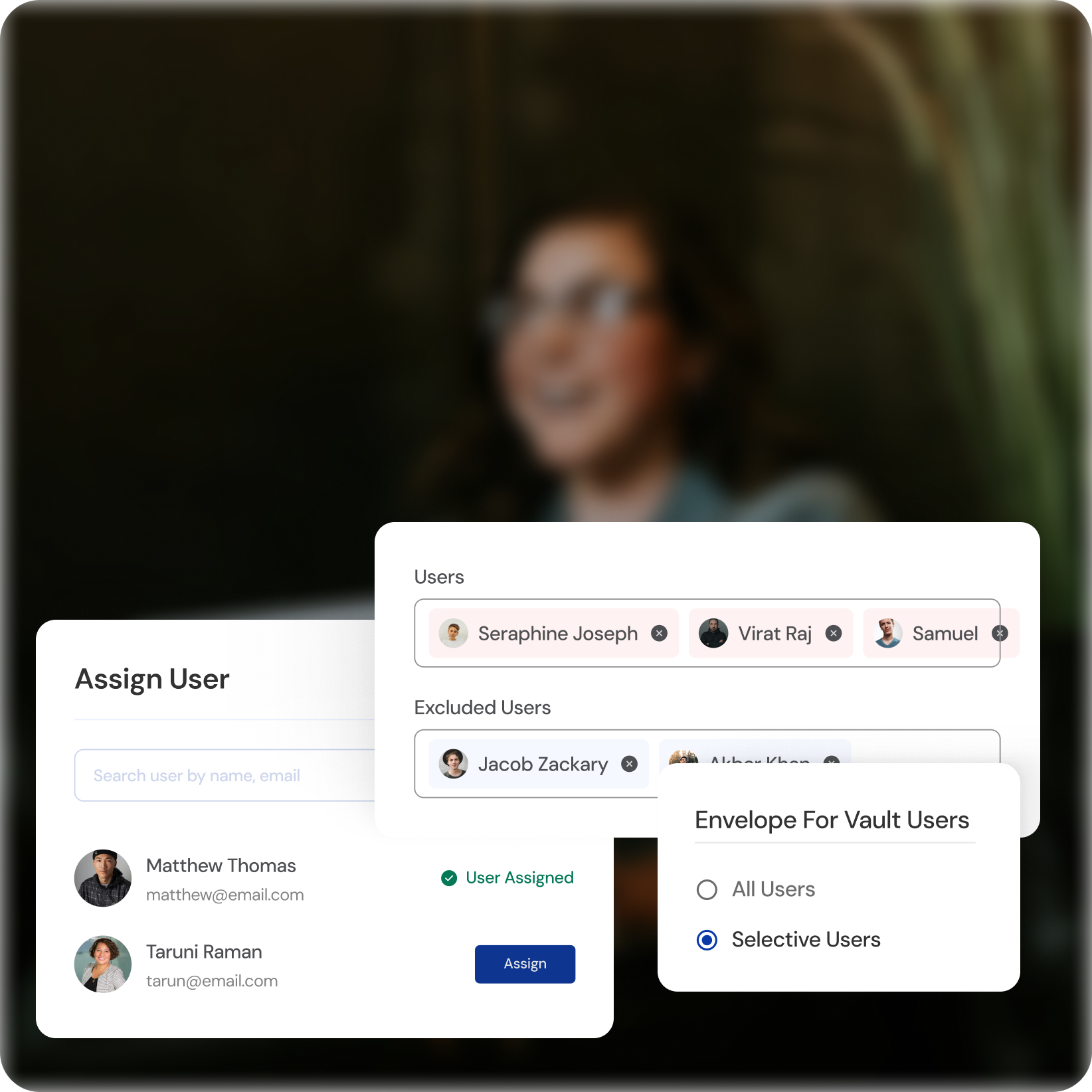
Granular Access Control
Role-Based Permissions
Define access levels based on user roles and responsibilities, ensuring they only access the resources they need.
Reduced Attack Surface
Minimize the number of users with elevated privileges, shrinking the potential attack surface for malicious actors.
Flexible Control
Manage access at various levels (applications, systems, specific actions) depending on your organization's needs.
KEY ADVANTAGES
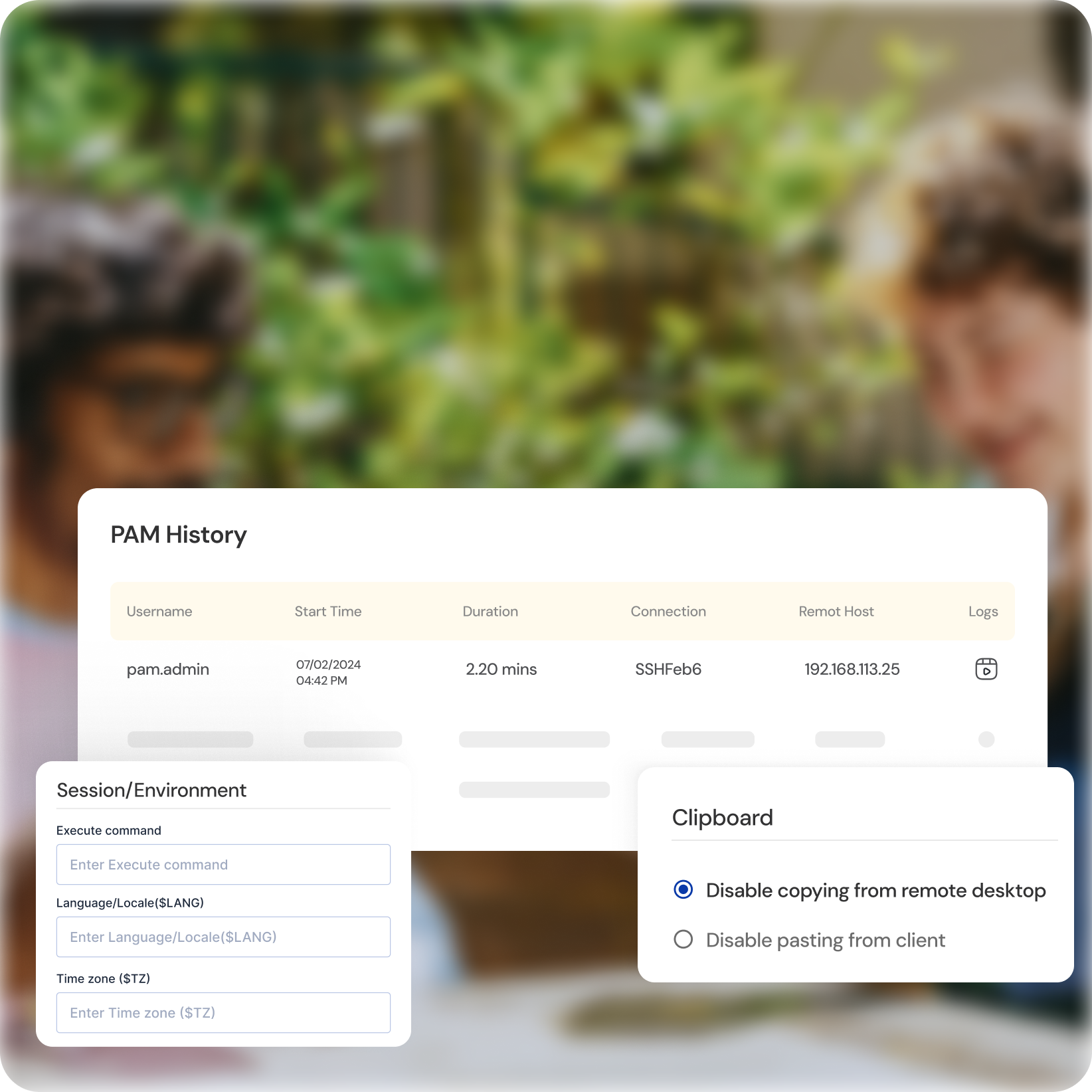
Session Monitoring and Recording
Real-Time Visibility
Gain real-time insights into privileged user activity with detailed session monitoring, including recording keystrokes and screenshots.
Forensic Analysis
Investigate suspicious behavior quickly and effectively with recorded sessions for deeper analysis and evidence collection.
Enhanced Accountability
Improve user accountability and deter unauthorized access by knowing their actions are monitored.
KEY ADVANTAGES
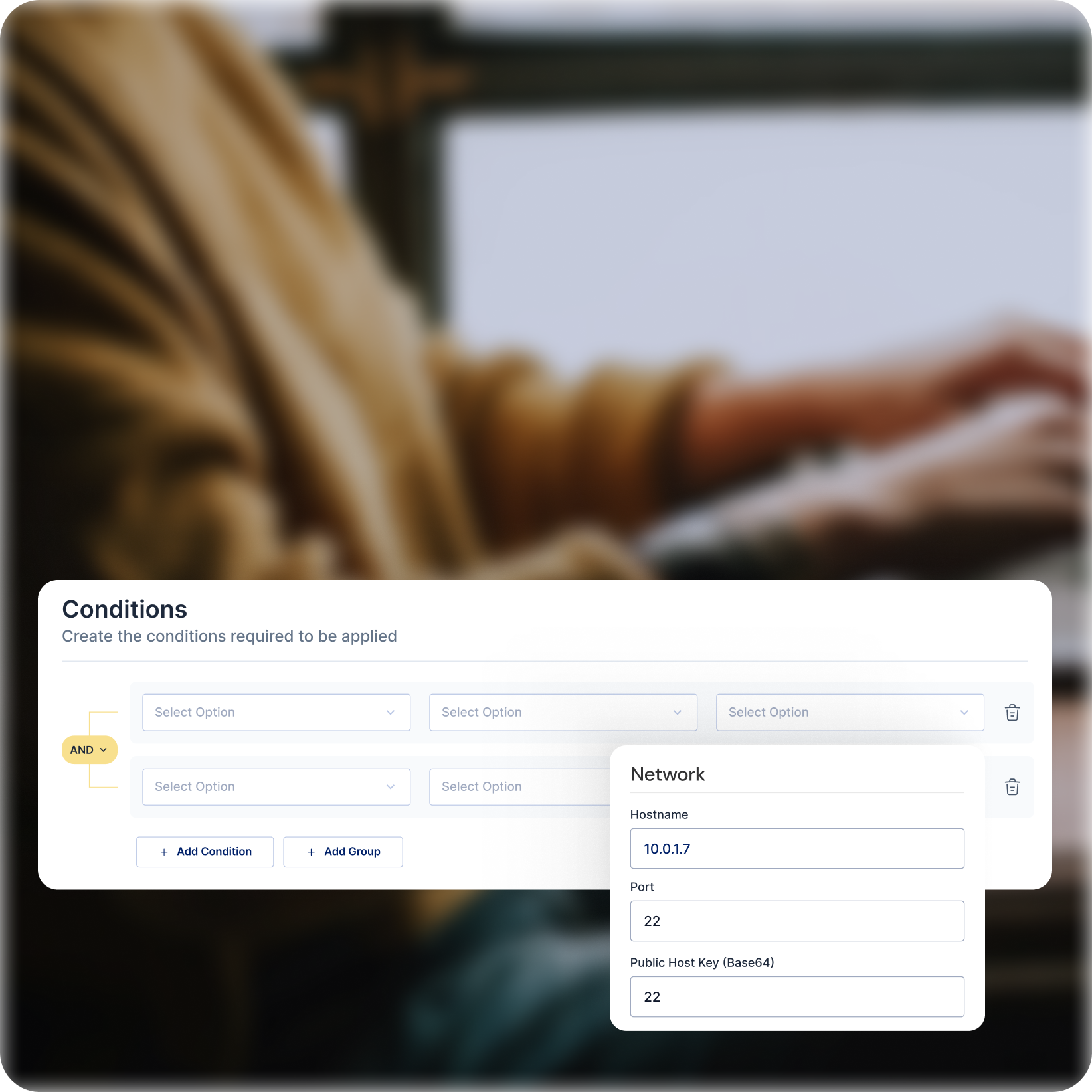
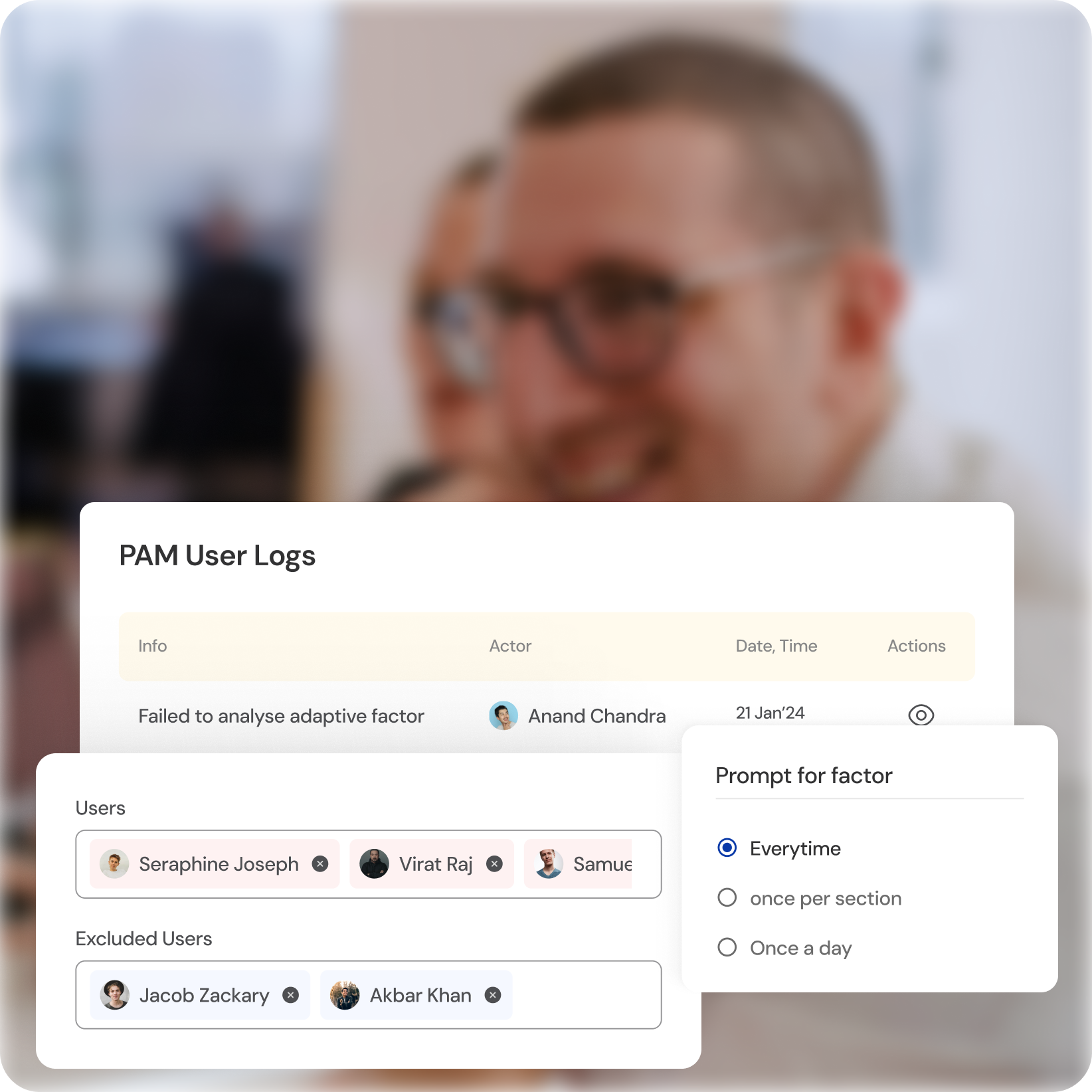
Elevated Access Approval Workflows
Multi-Factor Authentication (MFA)
Add an extra layer of security by requiring additional verification factors for privileged access requests.
Approval Workflows
Implement approval processes for critical access requests, involving additional team members or security personnel.
Reduced Risk of Accidental Misuse
Prevent unauthorized access attempts and accidental privilege escalation with controlled approval workflows.
KEY ADVANTAGES
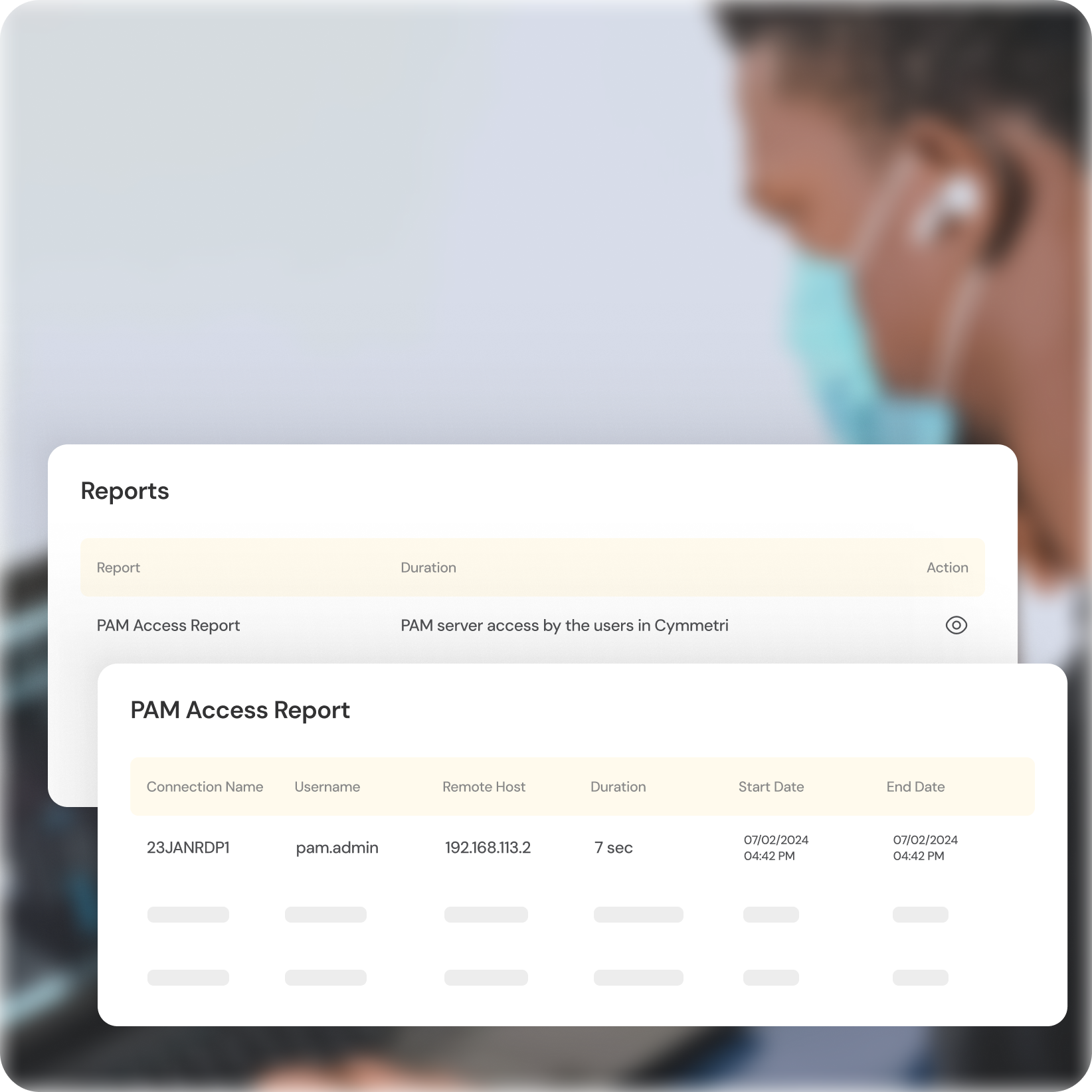
User Activity Reporting
Comprehensive Reports
Gain valuable insights into privileged user activity with detailed reports on access attempts, successful sessions, and potential anomalies.
Identify User Behavior Patterns
Monitor trends and identify suspicious activity patterns that could indicate potential threats.
Compliance Adherence
Generate reports to demonstrate compliance with internal security policies and industry regulations.
KEY ADVANTAGES
Benefits of Cymmetri PAM
Mitigate Risk of Unauthorized Access
Secure privileged accounts with central password management, granular access control, and user activity monitoring.
Strengthen Security Posture
Implement MFA and approval workflows for elevated access, significantly reducing the risk of breaches.
Improve Operational Efficiency
Streamline password management and access requests, saving time and resources for your IT team.
Enhanced Visibility and Accountability
Gain real-time insights into user activity and improve user accountability, deterring potential misuse."
IDENTITY HUB
Other Cymmetri Products to help your Business








