New Feature Alert - CISO DashboardCheckout Now
350+
Integrated Applications
3M+
Identities protected
5$
per user saved for Governance and Reports
KEY ADVANTAGES
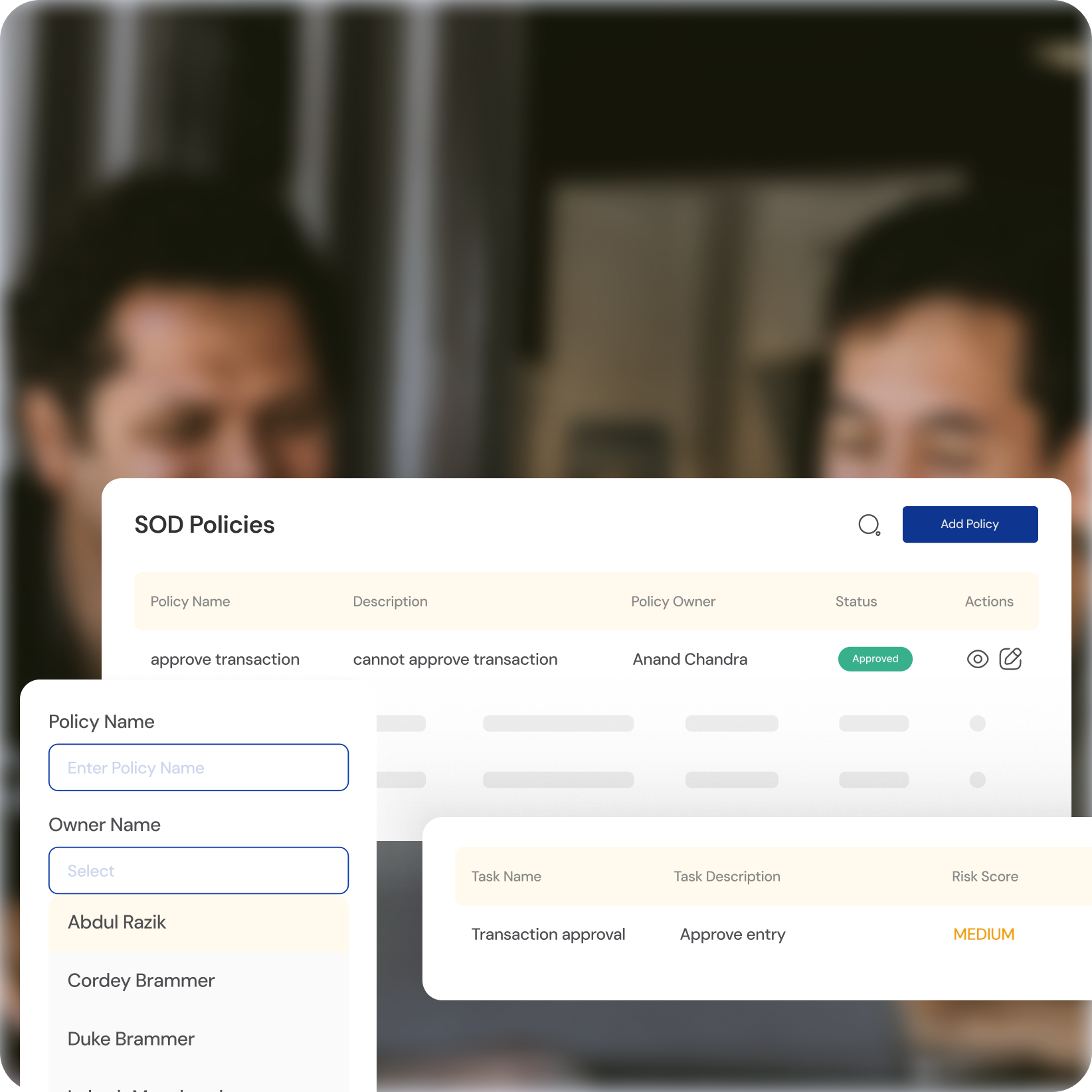
Empower Security with Robust Segregation of Duties (SoD)
Minimize Risk
Enforce stricter SoD policies to prevent unauthorized access and potential breaches. Reduce the risk associated with shared privileges and build a more resilient security posture. experience.
Clear Accountability
Ensure clear lines of responsibility and control through granular access management. Empower informed access decisions and minimize the risk of fraud or errors.
Tailored SoD
Shape a secure and customized SoD framework that aligns with your organization's specific needs and compliance requirements.
KEY ADVANTAGES
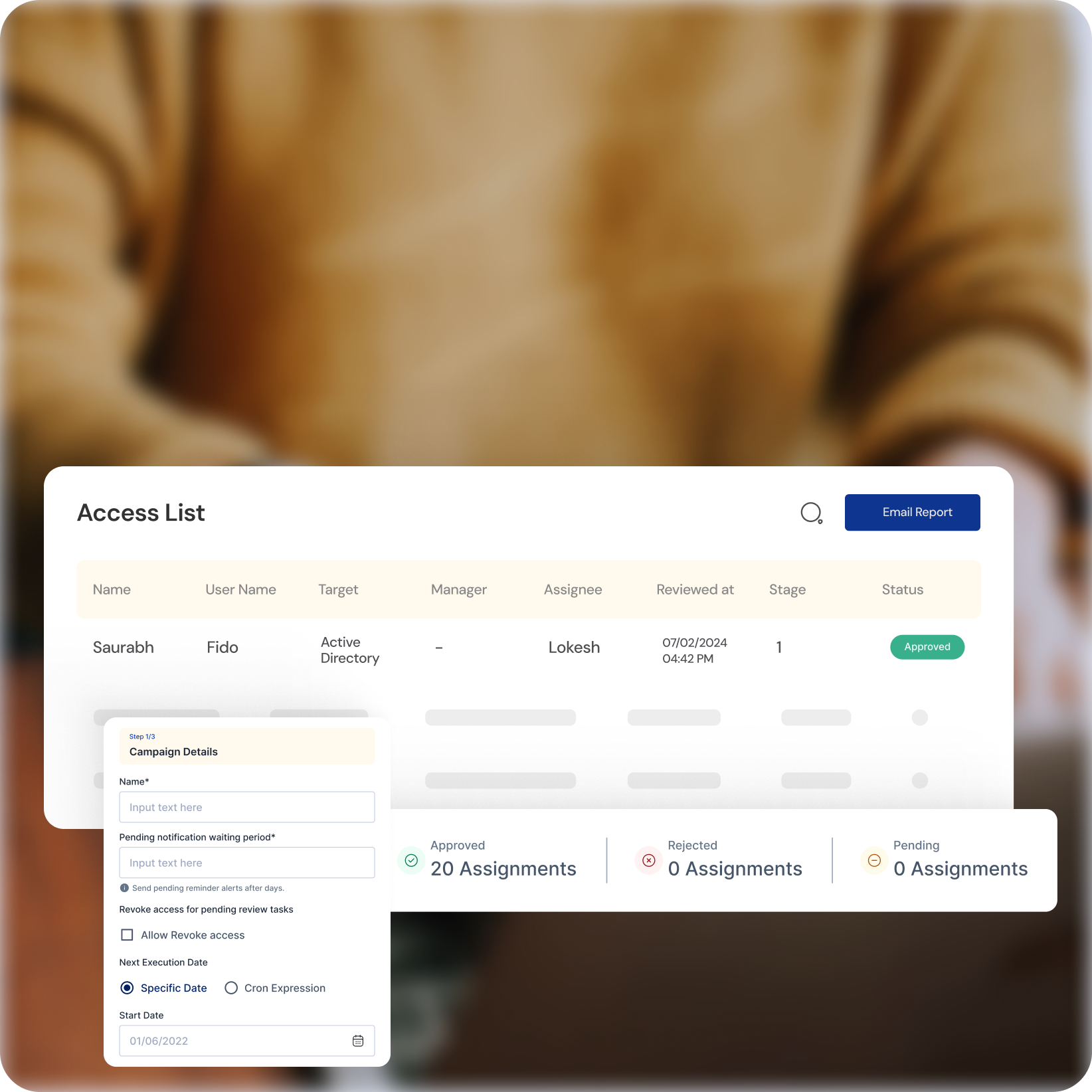
Continuous Monitoring for Comprehensive Access Reviews
Go Beyond Traditional
Leverage continuous monitoring to identify and address access anomalies in real-time, ensuring only authorized users access critical systems.
Proactive Threat Detection
Instantly identify and respond to suspicious access attempts with real-time anomaly detection, neutralizing potential threats before they escalate.
Streamlined Reviews
Simplify access review processes with a centralized platform, automating tasks and ensuring timely completion of certifications, reducing administrative burden.
KEY ADVANTAGES
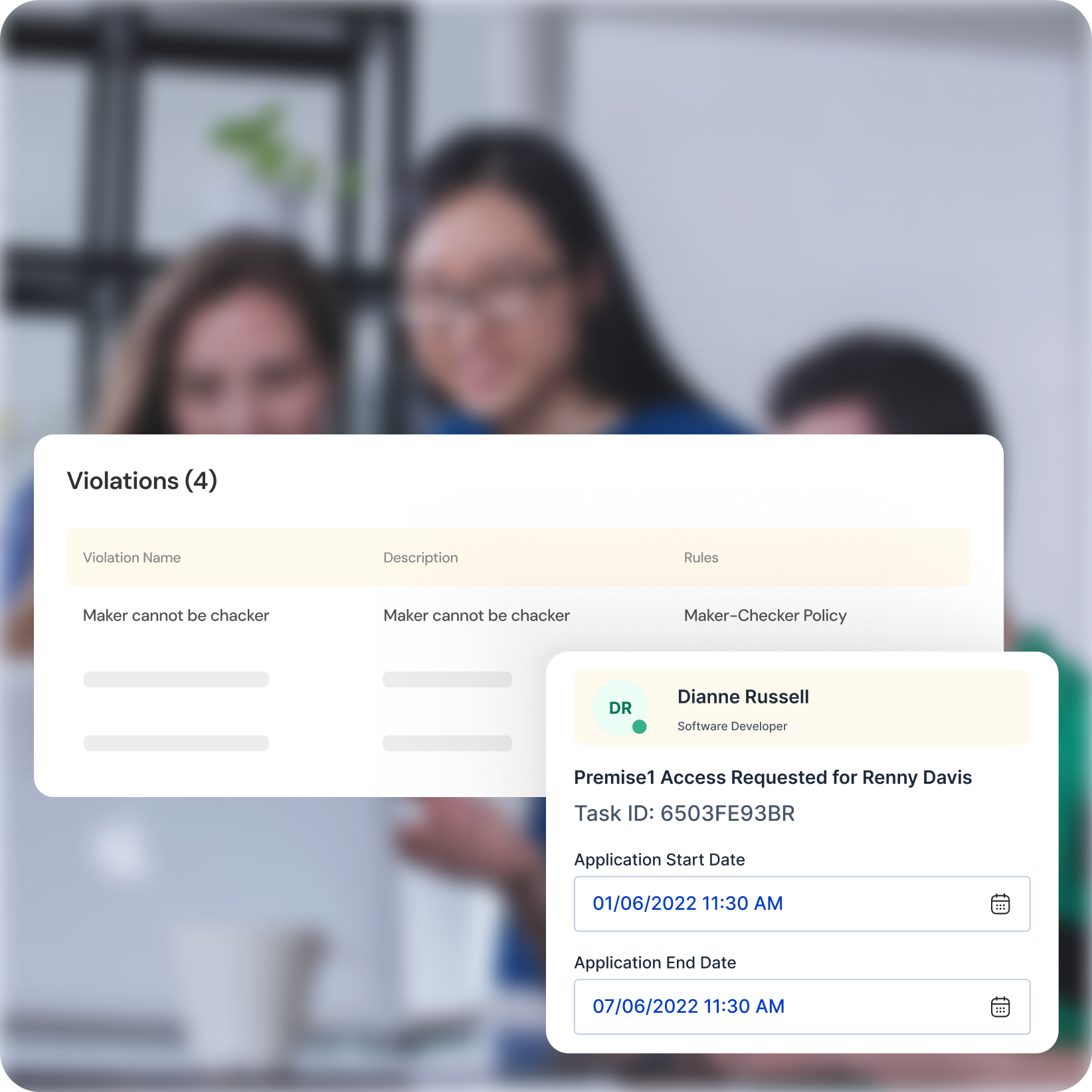
Unified Security with Integrated Solutions
Seamless Integration
Seamlessly integrate SoD and access review functionalities with your existing identity governance platform, creating a unified security infrastructure that simplifies management and streamlines operations.
Holistic Approach
Embrace a holistic identity governance approach by addressing both SoD and access review needs with a single, comprehensive platform.
Future-Proof Security
Cater to the evolving needs of your organization in the digital age with a scalable and adaptable solution, ensuring compliance with regulations and preparing for future security challenges.
KEY ADVANTAGES
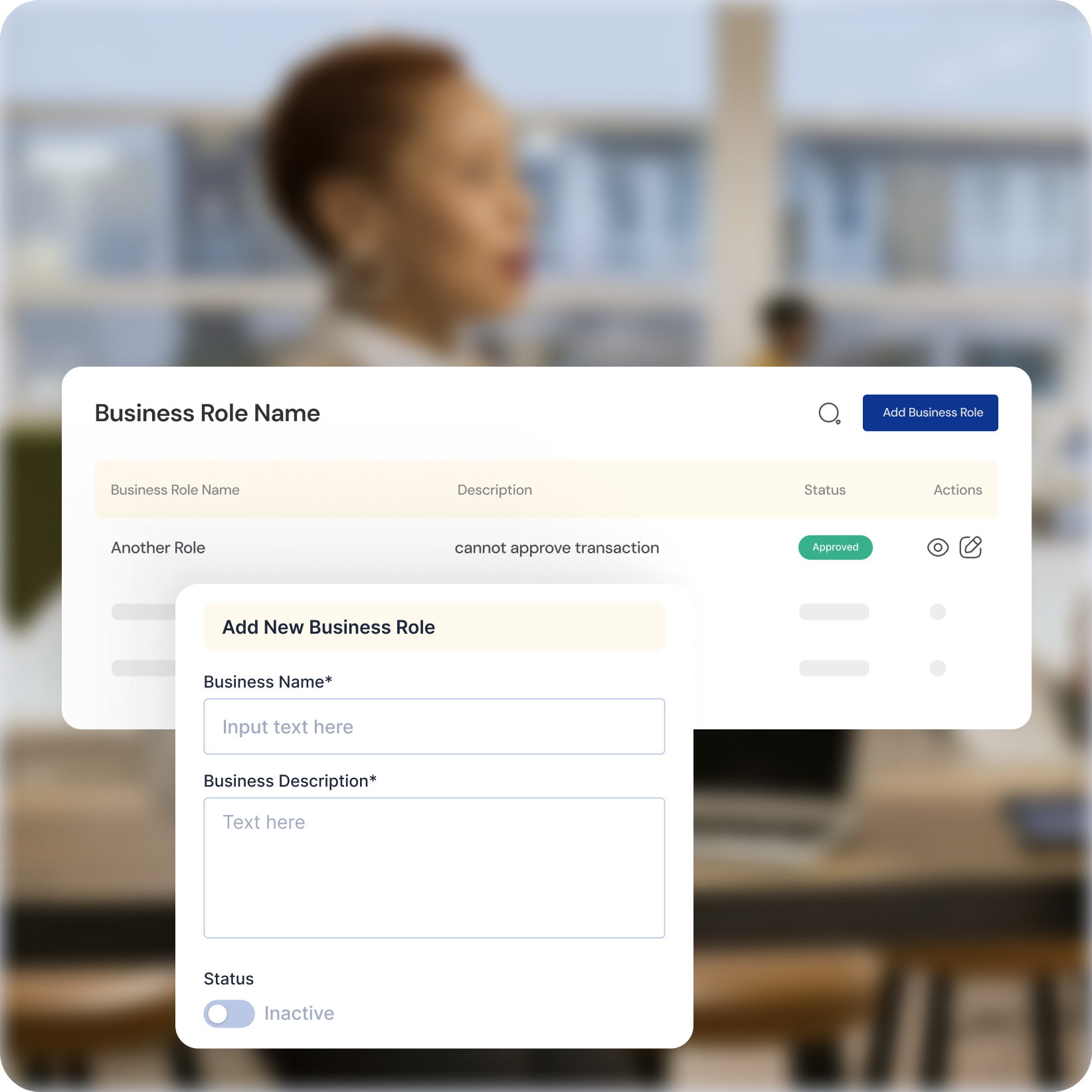
Resolving Role Conflicts for Optimal Access Control
Proactive Conflict Identification
Automatically identify and prioritize role conflicts that could lead to security vulnerabilities.
Streamlined Resolution
Utilize intuitive tools to define, control, and resolve role conflicts efficiently, ensuring a secure and efficient access framework.
Nuanced Access Management
Empower granular access control with role-based permissions and least privilege principles, minimizing risk and optimizing efficiency.
IDENTITY HUB
Other Cymmetri Products to help your Business








