New Feature Alert - CISO DashboardCheckout Now
350+
Integrated Applications
3M+
Identities protected
5$
per user saved for Governance and Reports
KEY ADVANTAGES
Streamlined User Onboarding & Offboarding
Efficient Onboarding
ILM automates the process of provisioning new user accounts, ensuring a smooth and quick onboarding experience.
Secure Offboarding
When employees leave the organization, ILM ensures their access is promptly revoked, reducing the risk of unauthorized access post-employment.
Access Control
Cymmetri ILM ensures that users have the right level of access based on their roles and responsibilities. This reduces the risk of unauthorized access to sensitive data and applications.
KEY ADVANTAGES
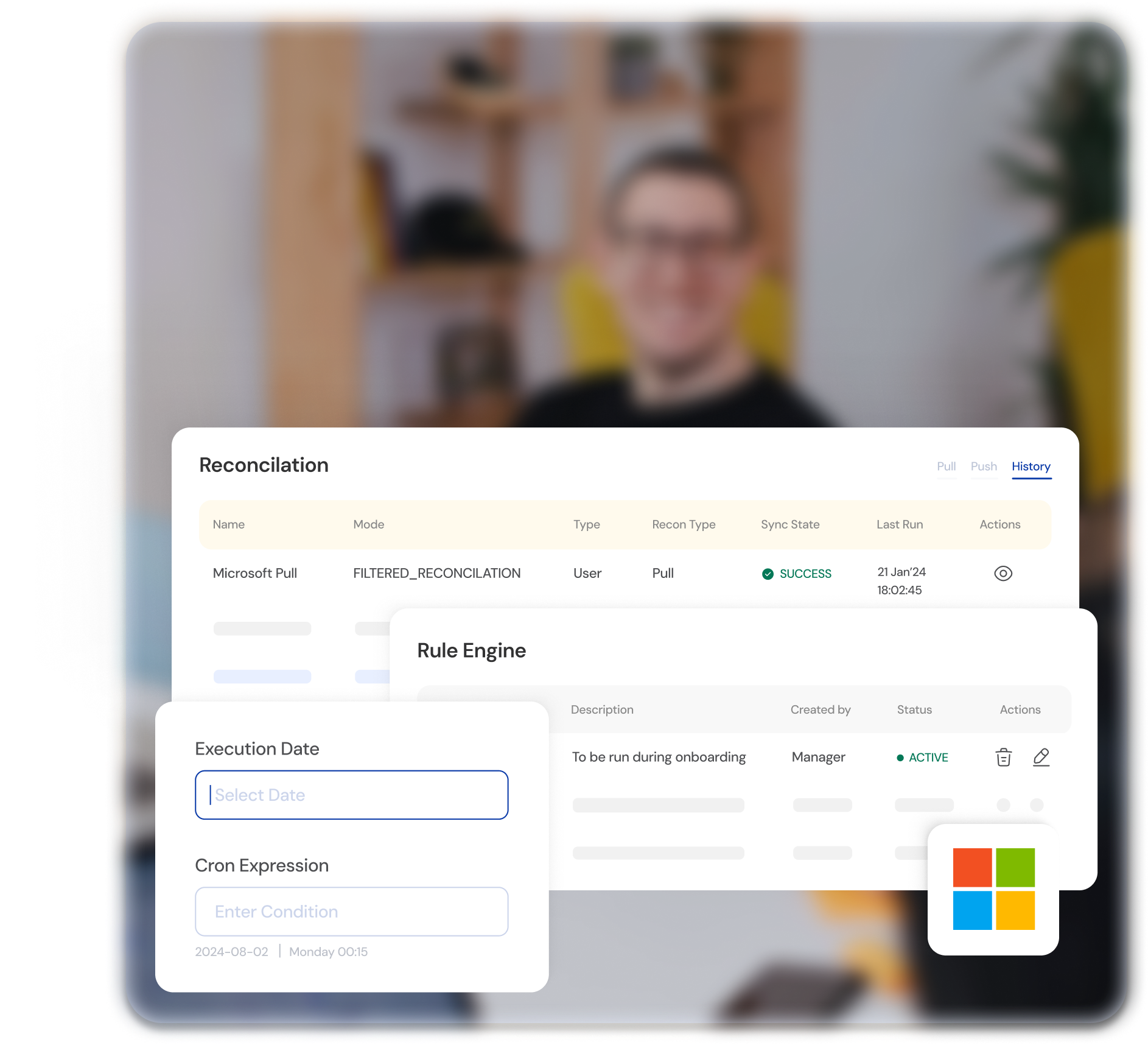
Increased Operational Efficiency & Reduce Cost
Automation
ILM automates routine identity management tasks, reducing manual workload for IT teams and minimizing the likelihood of errors.
Self-Service Options
User self-service capabilities for password resets, profile updates, and access requests empower users and reduce the burden on IT support.
Efficient Resource Allocation
ILM allows organizations to allocate resources more efficiently by automating repetitive tasks, leading to cost savings in terms of time and manpower.
Risk Mitigation
By minimizing the risk of security breaches and ensuring compliance, ILM helps prevent costly consequences associated with data breaches and regulatory non-compliance.
KEY ADVANTAGES
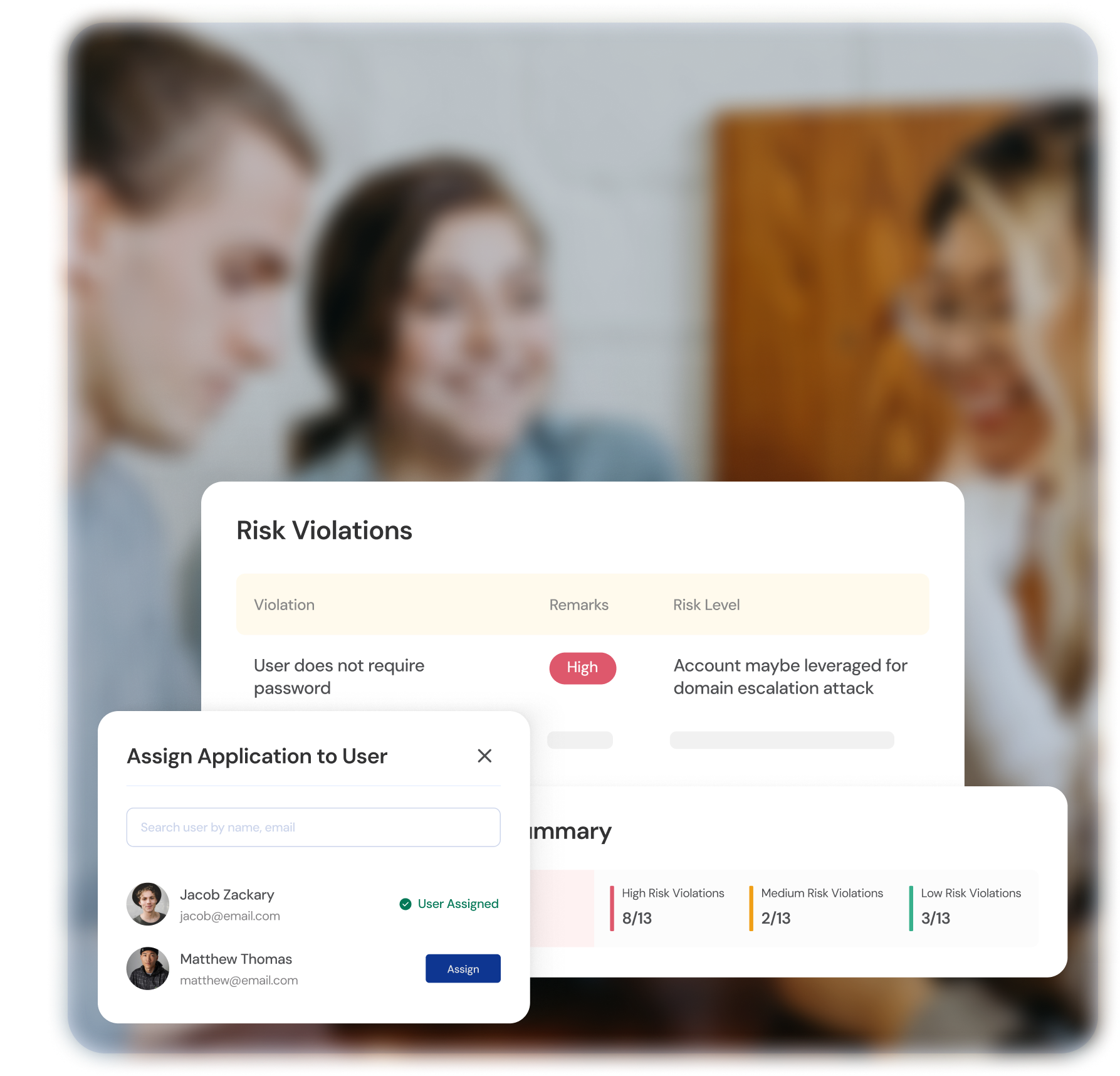
Enhanced User Experience
User Self-Service
Providing users with the ability to manage their own profiles and access rights enhances the overall user experience.
Reduced Friction
ILM minimizes disruptions by ensuring that users have the necessary access to perform their roles without unnecessary delays or obstacles.
Multi-Factor Authentication (MFA)
Implement multi-layered authentication for robust protection.

KEY ADVANTAGES
Centralized Management
Single Point of Control
ILM provides a centralized platform for managing user identities, making it easier to monitor and control access across the organization.
Consistent Policies
Implementing consistent identity management policies ensures uniformity and reduces the risk of inconsistencies or oversights.

KEY ADVANTAGES
Flexibility and Scalability
Adaptability
ILM solutions can be tailored to suit the unique needs and workflows of different businesses.
Scalability
As businesses grow, ILM can scale to accommodate an increasing number of users and evolving security requirements.
KEY ADVANTAGES
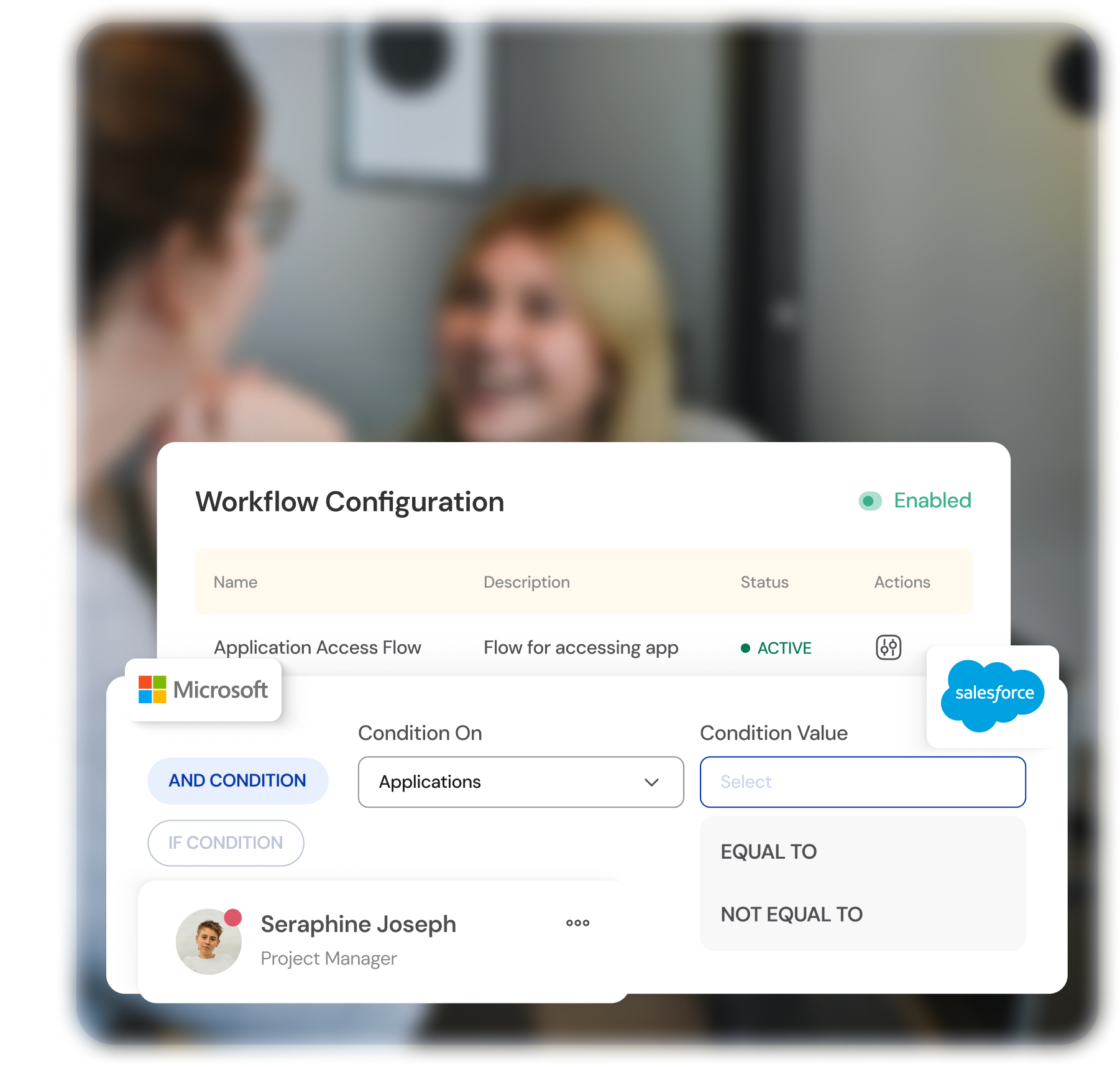
Improved Compliance
Audit Trails
ILM solutions maintain detailed logs of user activities, facilitating compliance with industry regulations and internal policies.
Role-Based Access Control
Align user access permissions with regulatory requirements, ensuring that users only have access to information relevant to their roles.
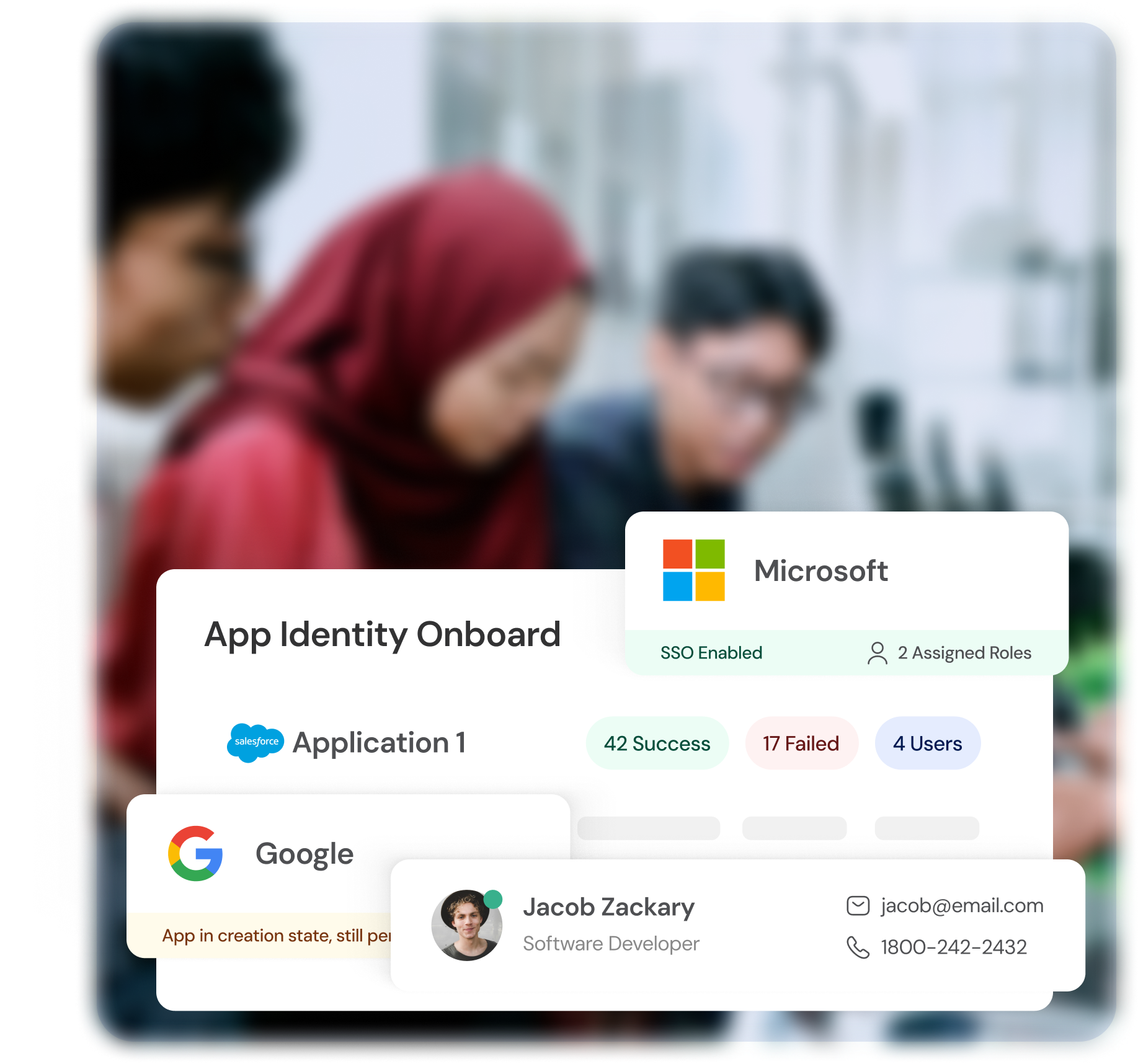
IDENTITY LIFECYCLE MANAGEMENT
Other Cymmetri Products to help your Business