New Feature Alert - CISO DashboardCheckout Now
350+
Integrated Applications
3M+
Identities protected
5$
per user saved for Governance and Reports
KEY ADVANTAGES
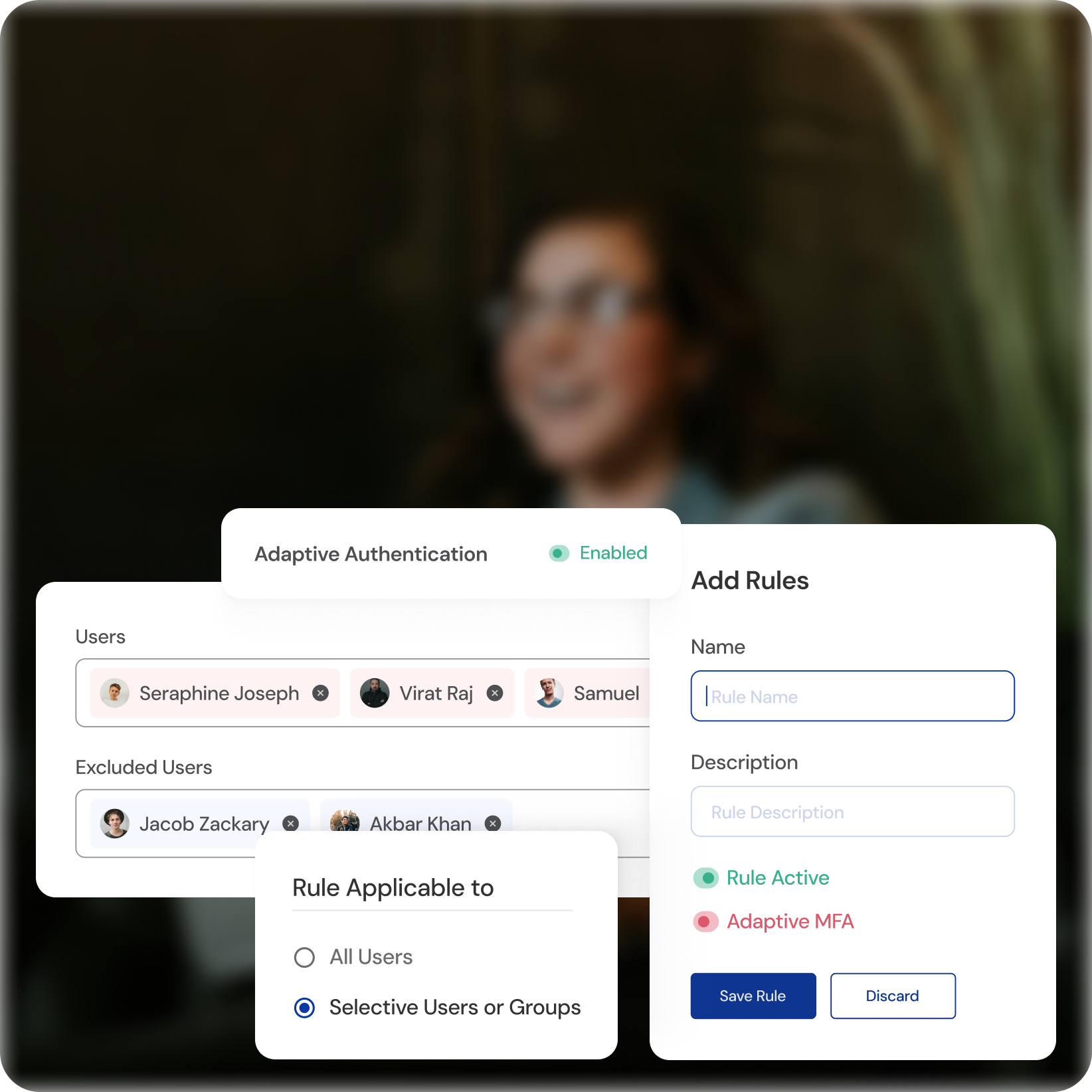
Dynamic Multi-Factor Authentication (MFA)
Unprecedented Versatility
Choose from various verification methods including passwords, biometrics, and one-time passcodes.
Tailored for Every Need
Adapt authentication flows based on user roles, access levels, and risk contexts.
Frictionless Experience
Secure your systems while maintaining a smooth and efficient user experience.
KEY ADVANTAGES
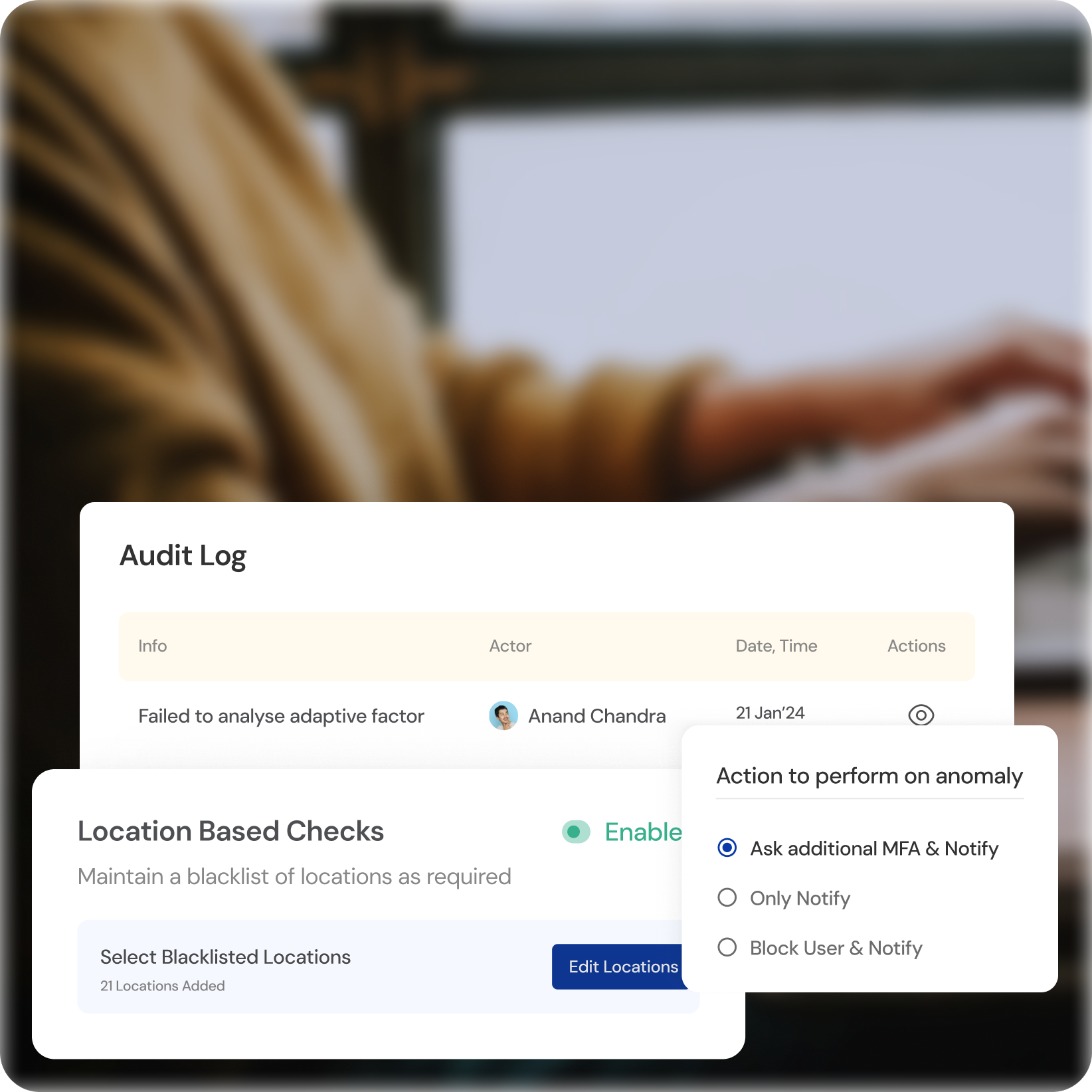
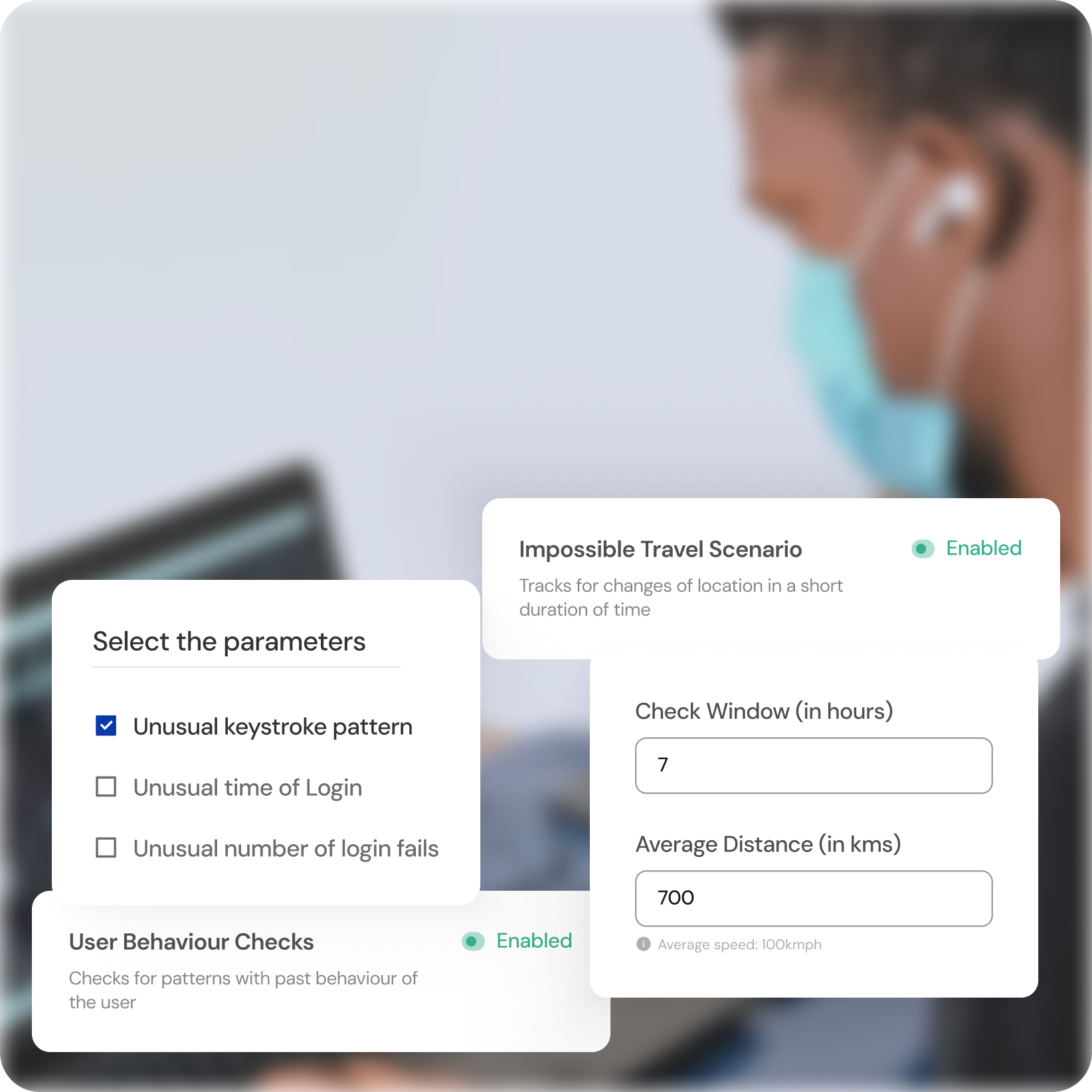
Intelligent Behavioral Analytics
Real-time Threat Detection
Uncover suspicious activity by continuously analyzing user behavior patterns.
Proactive Response
Identify and neutralize potential threats before they cause harm.
Continuous Learning
The system adapts and learns, continually improving its ability to detect anomalies.
KEY ADVANTAGES
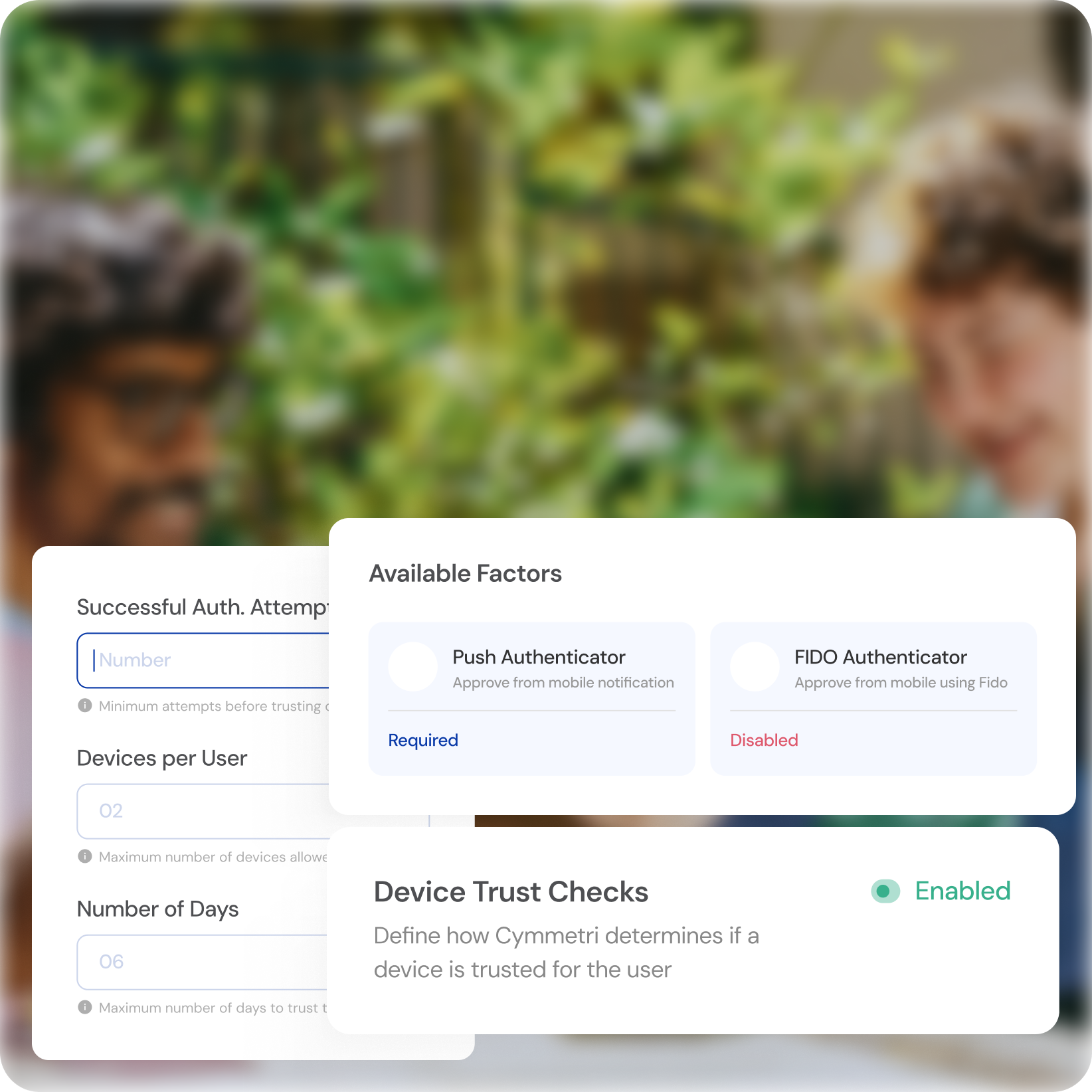
Seamless Device Recognition
Effortless Convenience
Gain automatic access from trusted devices, reducing login fatigue.
Enhanced Security
Trigger additional authentication steps for unrecognized or risky devices.
Granular Control
Define trusted device criteria based on location, network, and device characteristics.
KEY ADVANTAGES
Tailored Risk-Based Authentication
Dynamic Security Levels
Adjust authentication strength based on individual user risk profiles and access attempts.
Adaptive Approach
Balance convenience with security, ensuring appropriate protection for varying scenarios.
Risk-aware Decisions
Focus resources on high-risk activities while streamlining low-risk interactions.
KEY ADVANTAGES
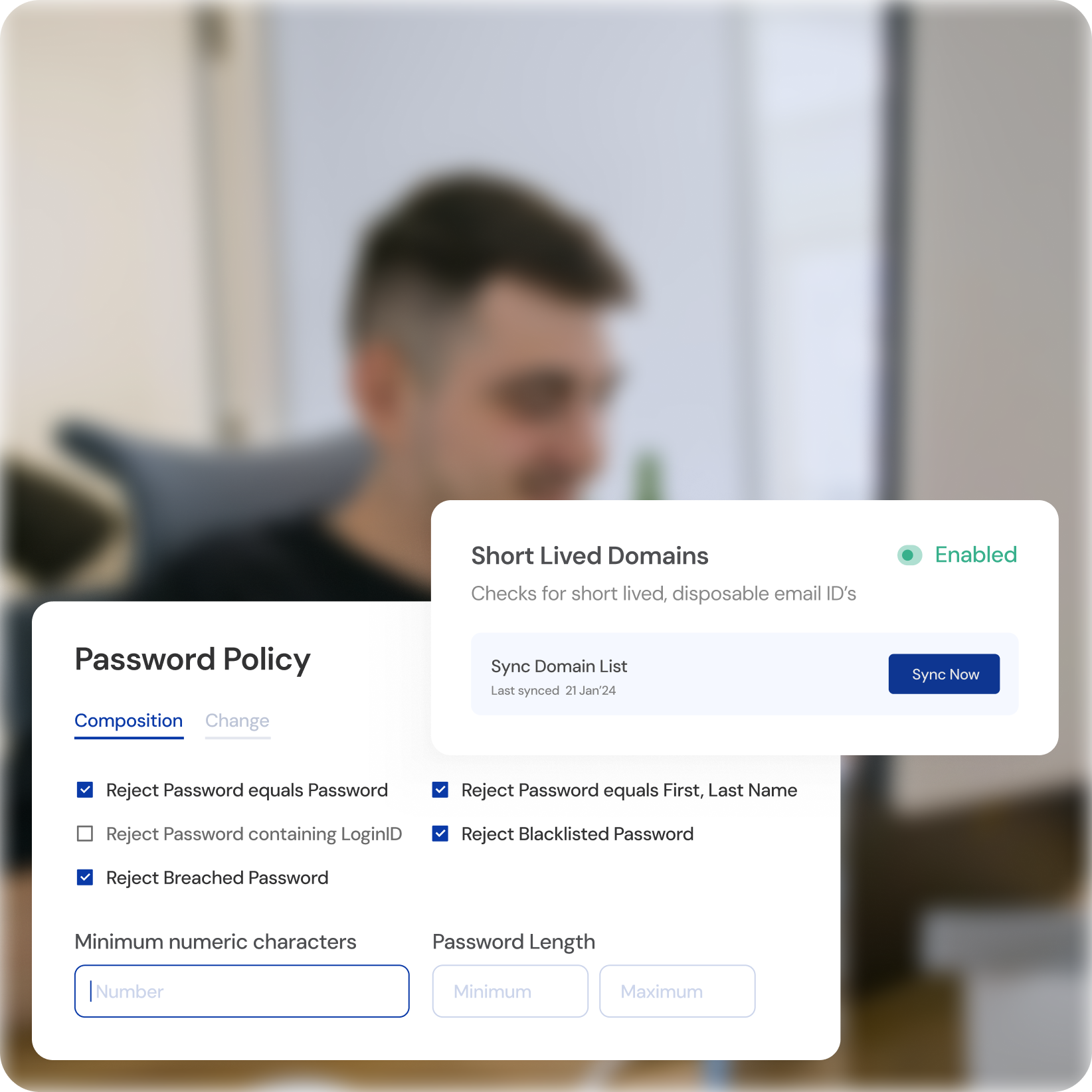
Adaptive Learning and Continuous Monitoring
Machine Learning Powered
Leverage advanced algorithms to identify and respond to emerging threats.
Automated Threat Detection
Proactively mitigate risks without requiring manual intervention.
Continuous Adaptation
The system evolves alongside cyber threats, ensuring ongoing protection.
Adaptive Authentication
Other Cymmetri Products to help your Business








