New Feature Alert - CISO DashboardCheckout Now
350+
Integrated Applications
3M+
Identities protected
5$
per user saved for Governance and Reports
KEY ADVANTAGES
Break Down Silos, Build a Single Source of Truth
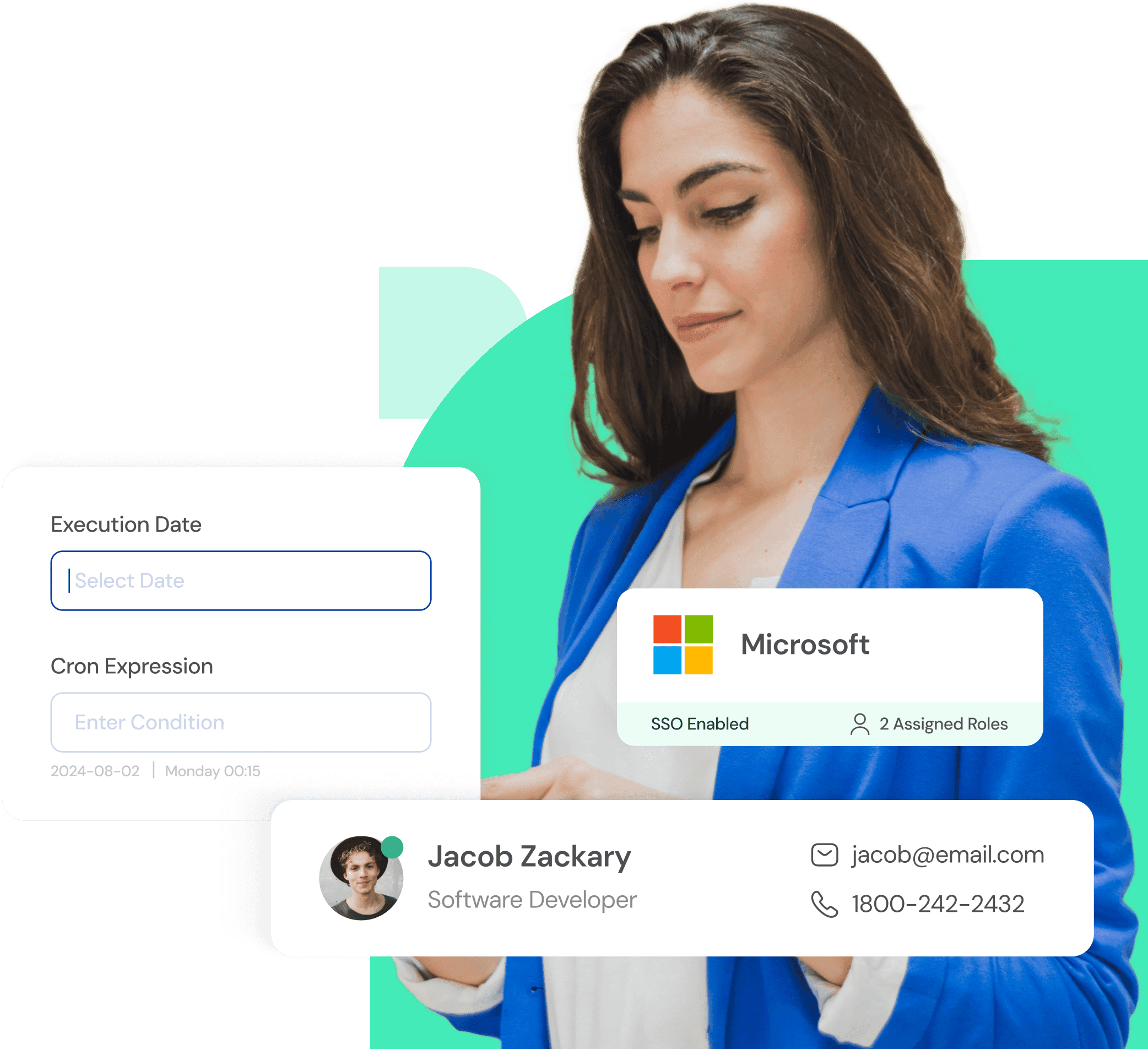
Eliminate Disconnected Data
Consolidate user identities across cloud, SaaS apps, databases, and on-premises systems.
Gain Holistic Visibility
View user profiles, attributes, and access rights in one central location.
Simplify Compliance Audits
Easily meet data privacy regulations like GDPR and CCPA with complete transparency.
KEY ADVANTAGES
Streamline User Management, Boost Efficiency
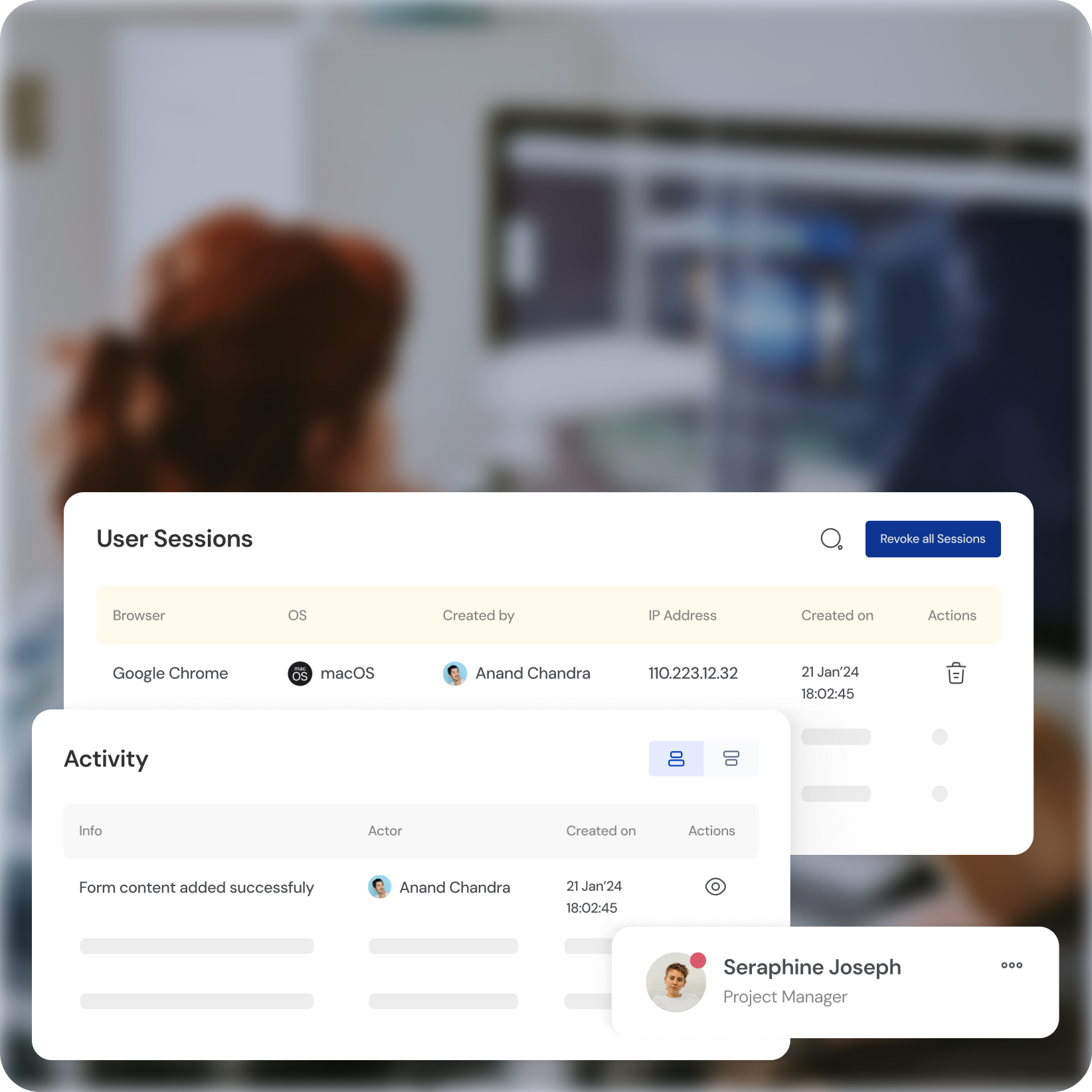
Automated Onboarding & Offboarding
Automate user provisioning and deprovisioning, saving IT time and resources.
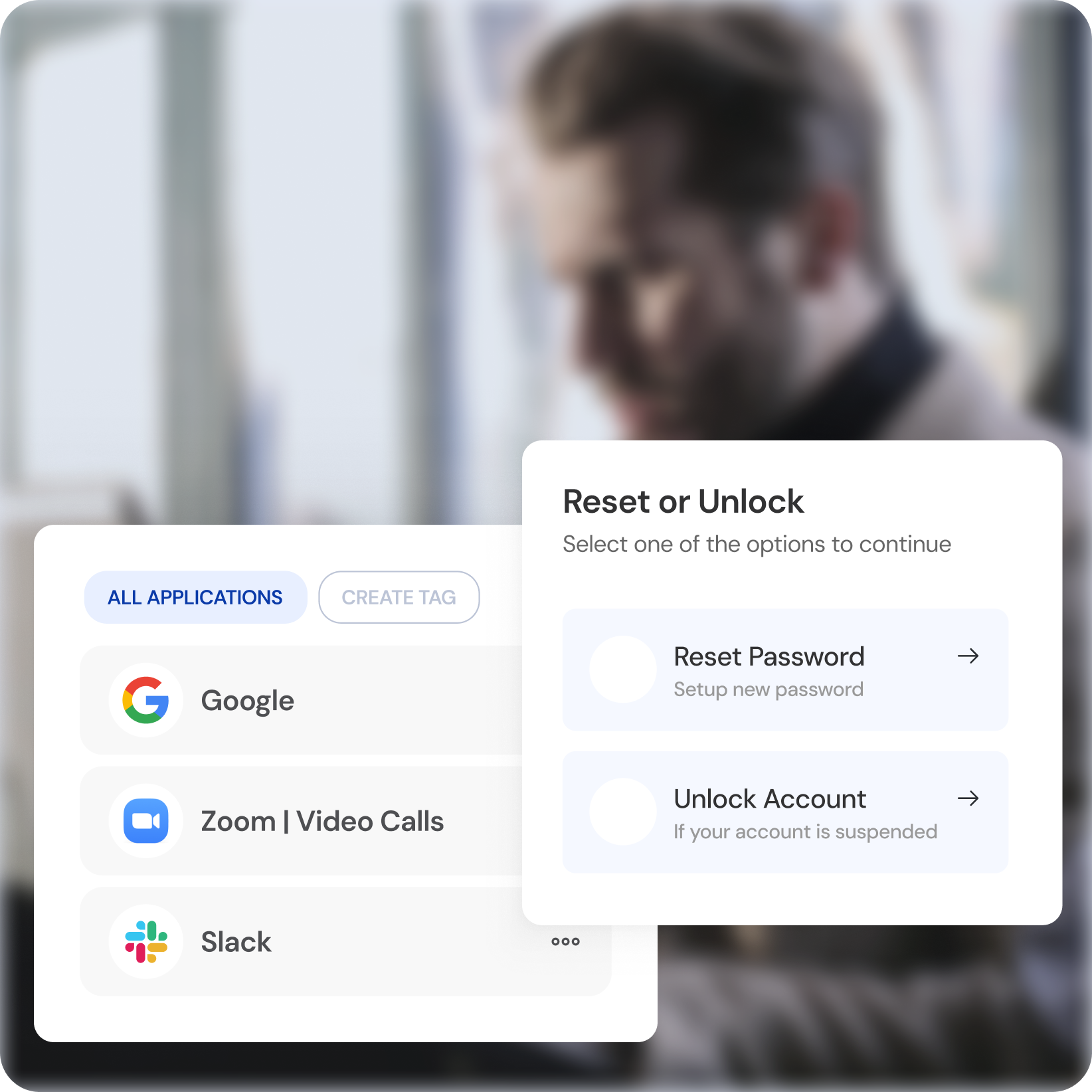
Self-Service Access Requests
Empower users to request and manage their own access permissions.
Streamlined Approval Workflows
Reduce administrative burden with efficient approval processes.
KEY ADVANTAGES
Fortify Security, Minimize Risk
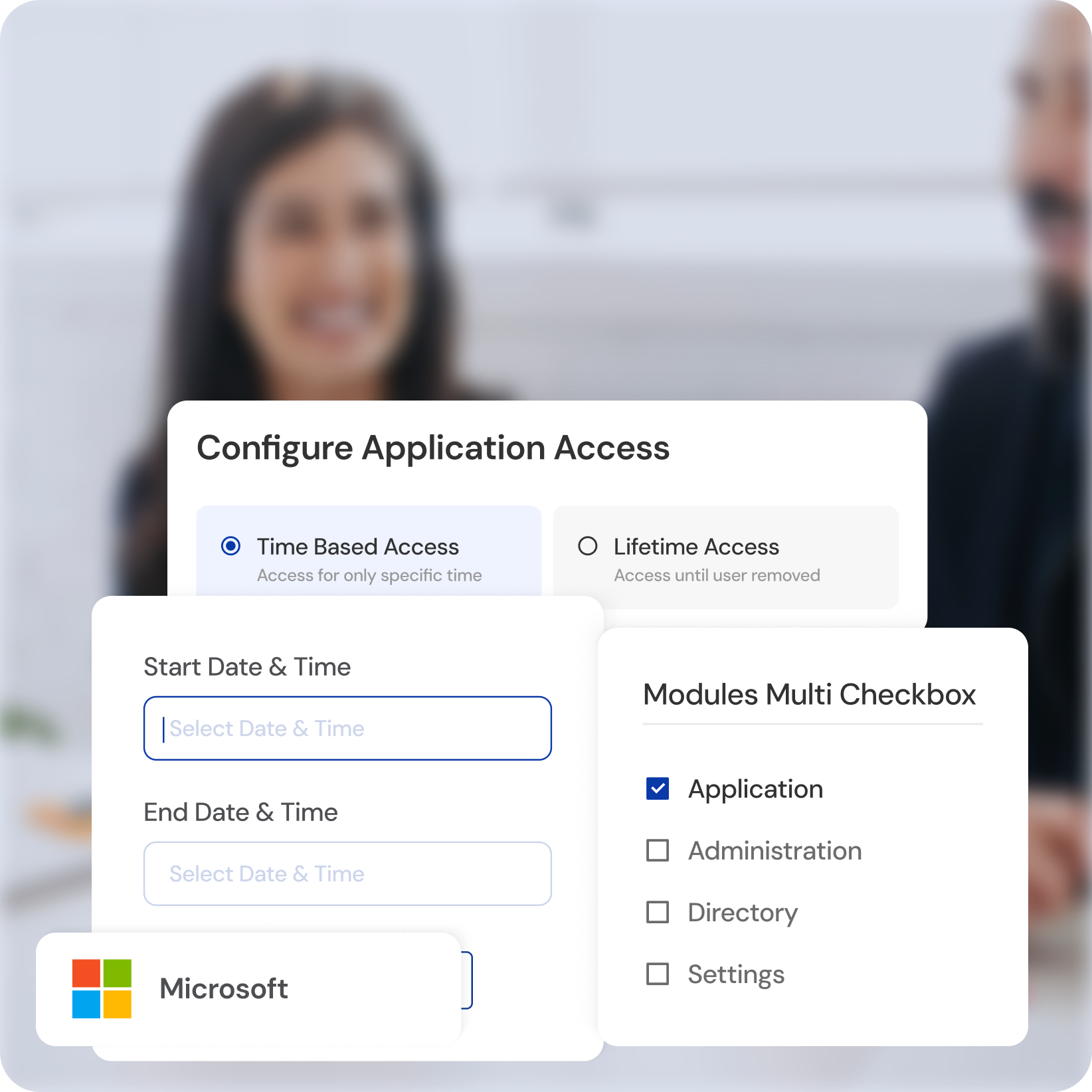
Granular Access Control
Grant fine-grained access based on roles, departments, and specific needs.
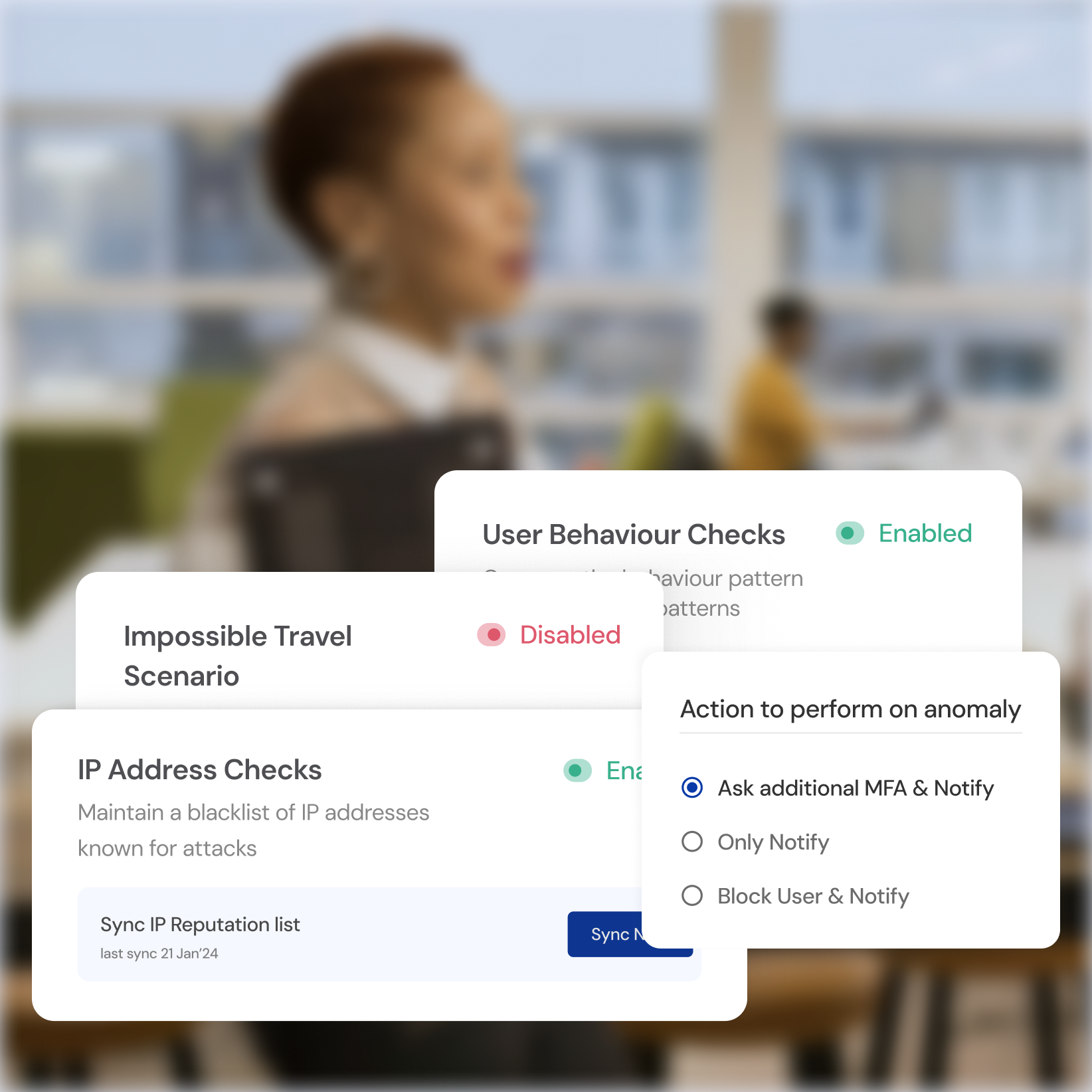
Real-time Threat Detection
Identify and mitigate suspicious activity with behavioral analytics.
Multi-Factor Authentication (MFA)
Implement multi-layered authentication for robust protection.
KEY ADVANTAGES
Enhance User Experience, Drive Productivity
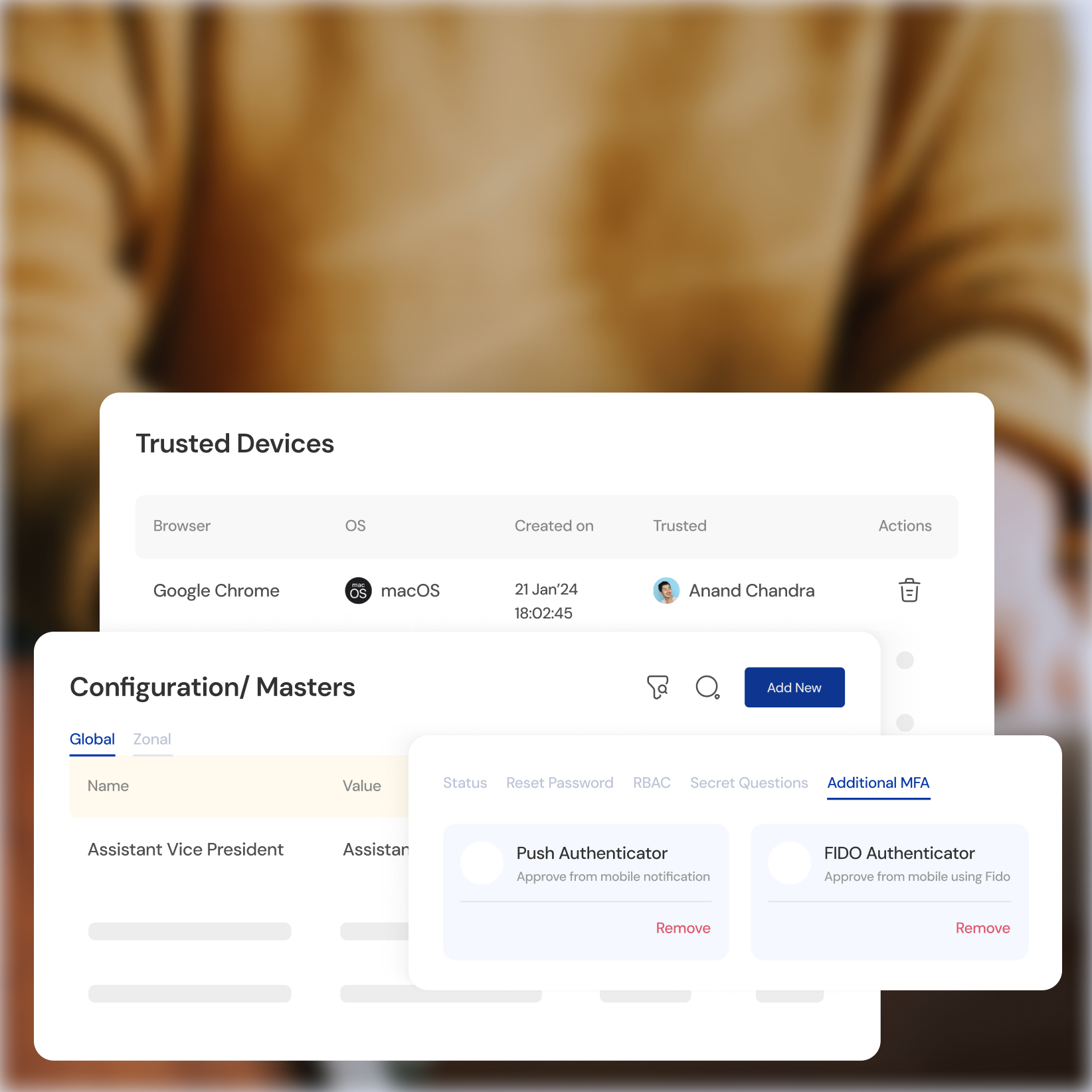
Single Sign-On (SSO)
Provide seamless access to all applications with a single login.
Self-Service Password Management
Empower users to reset passwords independently.
Mobile-Friendly Access
Securely access resources from any device, anytime, anywhere.
KEY ADVANTAGES
Embrace the Future of Identity Management
AI-Powered Insights
Gain deeper understanding of user behavior and access patterns.
Adaptive Risk-Based Authentication
Dynamically adjust security based on individual risk profiles.
Future-Proof Scalability
Adapt to your growing user base and evolving security needs.
IDENTITY HUB
Other Cymmetri Products to help your Business